
As companies begin upgrading from card-based access control systems to Mobile Access Control, there is a widespread misunderstanding that mobile is less secure. This seems to be based on the idea that an RFID entry card is designed solely for the purpose of access control, therefore it must be more secure. Nothing could be further from the truth.
- Card-based access control has become more secure
The very first card-based access, introduced in the mid 1970s, relied on magnetic stripe cards. These were prone to failure and extremely easy to copy. Around 1990, companies replaced these with cards that used 125 kHz radio frequencies (the RF in RFID) to communicate with a reader. These were more reliable, but simply passed along an unencrypted 26-byte key through the air. These fully unencrypted cards still make up about 20% of the market. Thieves can clone them from several meters away.
Around 2010, manufacturers introduced a new series of cards using a higher frequency 13.56 MHz signal, and introducing encryption. These cards each had a unique ID, meaning employers could also use them to track time and attendance. While early versions of these 13.56 MHz cards were ultimately hacked, newer cards with 128-bit AES encryption have not yet been compromised.
- Lost and Stolen Cards are a Security Risk
Still, cards are physical credentials, often integrated into a badge with the company name on it. People leave them on tables at cafes. They leave them in their cars. They drop them from their pockets when they reach in to get their keys. Lost and stolen cards represent a major security risk to companies.
- Why mobile access control promises to be more secure
Instead of using passive RFID cards, Mobile Access Control uses newer Near Field Communication (NFC) and Bluetooth Low Energy (BLE). Both technologies are used for contactless exchange of data and are at least 20 years newer than RFID technology. Nearly all smartphones sold since 2015 include one or both of these communication standards.
NFC is a short-range technology that only works within a few centimeters. BLE can be used at distances up to 100 meters, but importantly also includes support for proximity sensing. Both support strong encryption protocols, and this strong encryption is key to good security.
While different manufacturers use different standards, a good Mobile Access solution uses 256-bit AES encryption to secure communication between phones and readers. This level of encryption would take billions of years to hack using today’s computers and a brute force attack.
Web-based platforms and apps are also another important technology feature of Mobile Access Control. They allow administrators to remotely issue or revoke credentials, without any need to provide or collect a physical security card. This has several practical advantages for security.
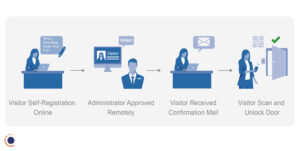
First, it means that anyone coming into a facility can have a mobile credential that gives them access only to the specific spaces they should be allowed to enter. Guests can only get into a specific meeting room. Delivery drivers can only enter the mailroom. Repair technicians can only enter the HVAC maintenance room. You get the idea.
Being able to remotely cancel credentials, or set them to expire automatically, significantly lowers the risks of lost or stolen cards. Disgruntled former employees cannot enter. The guy who delivers the water can only come into the office between 10 a.m. and 2 p.m.
Many companies are working to combine Mobile Access Control with digital ID to enhance role-based access. This will allow administrators to automatically allow or limit access to certain areas of a building based on certain pre-set criteria. For example, only employees who complete a wellness declaration will be allowed into the cafeteria. Only employees on Top Secret Project Team Z will be allowed into Conference Room B.
- Security Benefits beyond the Technology
While it may not seem like a technology, per se, people watch phones more closely than badges. They are significantly less likely to leave their phones laying around unguarded like they might with a company badge. Administrators can also require mobile credentials to work in “foreground” mode only, meaning that the phone has to be unlocked and the access control app must be open and active in order to unlock doors. This adds yet another layer of security.
Access control has advanced significantly since the early days of magnetic cards. Mobile access control systems make buildings safer than ever before, while actually improving convenience for employees, visitors, and even administrators. Selecting an access control system requires careful consideration of your specific needs and the solutions available.
Adapted from a&s Magazine

